





Home Site: http://www.missl.cs.umd.edu/wireless/eaptls/
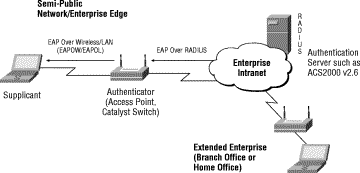
This document describes how to setup strong cryptographic authentication between XSupplicant and FreeRADIUS. This is accomplished using part of 802.1x authentication for wireless network. In particular it uses EAP/TLS extension, and TLS handshake.
The solution presented here is the first open source implementation of 802.1x.
The server side implementation in FreeRADIUS is courtesy of Raghu (raghud[at]hereuare.com), and XSupplicant was developed here at University of Maryland by Bryan D. Payne (bdpayne[at]cs.umd.edu) and Nick Petroni (npetroni[at]cs.umd.edu). The work on integration of those two programs was done by me, Adam Sulmicki (adam[at]cfar.umd.edu), with help from Yuan Yuan (yuanyuan[at]cs.umd.edu). Lots of thanks go to William A. Arbaugh (waa[at]cs.umd.edu) for making it all possible.
The good news is that all radiusd and xsupplicant patches towards their interoperatibility have been integrated into respective sources, so grabbing current cvs version is enough. No need to apply any patches. However, those stuff are highly experimental so additional software is required and extra steps in setup are needed so read on :-)
The system used for my setup is RedHat 7.2. From its default installation 'libnet' package is missing, so you will have to install it first. On similar token the EAP/TLS module for FreeRADIUS will require that you use snapshot version of openssl (along with stable version of openssl!). Instructions on how to get this software installed and runnings are below:
OpenSSL
LibNet
FreeRADIUS
XSupplicant
used by EAP/TLS module for FreeRADIUS
It is somewhat tricky. XSupplicant and FreeRADIUS in general will require stable version of SSL, but the EAP/TLS module requires latest snapshot (or any stable release after 1st March 2002, that is OpenSSL 0.9.7 or later), so generally you will have to have two versions of SSL and make sure EAP/TLS module is using the latest one and that *only* EAP-TLS is using it.
You will need *snapshot* version of SSL. The "stable-SNAP" will not do the trick, you need the one without word "stable". You are probably not interested in engine ("e") version neither as it is mostly for crypto _hardware_.
Just grab latest snapshot.
The snapshot I have used is
openssl-SNAP-20020227.tar.gz.
You can get latest snapshots from
ftp://ftp.openssl.org/snapshot/
http://www.openssl.org/
ftp://ftp.openssl.org/snapshot/openssl-SNAP-20020227.tar.gz
A
local copy is stored here : openssl-SNAP-20020227.tar.gz
mkdir -p /usr/src/802/openssl cd /usr/src/802/openssl ncftpget ftp://ftp.openssl.org/snapshot/openssl-SNAP-20020227.tar.gz tar zxvf openssl-SNAP-20020227.tar.gz cd openssl-SNAP-20020227 ./config shared --prefix=/usr/local/openssl make make install
NOTE: Since it is snapshot, as opposed to stable version, it is not recommended that you put it any "usual" places as --prefix=/usr or --prefix=/usr/local/ssl as it is to be used by EAP/TLS module in FreeRADIUS only.
After that you will probably want to edit /usr/local/openssl/ssl/openssl.cnf and customize it to your needs. example of possible customizations openssl.conf-diff. Customizing the file makes life easier when you want to generate your own set of keys and certificates. Other than that it is not necessary.
To generate your own set of keys you could use this script CA.all (NOTE: the script preset whatever password it can to 'whatever' so it is more for reference than anything else.). It will generate private key and off that private key it will generate CA, and then use that CA to generate two certificates ('client' and 'server' certificates).
You will also need 'random file' with (obviously) contains random data and another file to generate Diffie-Hellman key agreement.
Example set generated of OpenSSL is here cert.tgz. All passwords are set to 'whatever'.
Later examples assume you put those certificates in /etc/1x/r/ . For example to get them setup so using my set keys, you could just do :
mkdir -p /usr/src/802/keys cd /usr/src/802/keys wget http://www.missl.cs.umd.edu/~adam/802/keys/cert.tgz tar zxvf cert.tgz mkdir -p /etc/1x mv /usr/src/802/keys /etc/1x/
used by XSupplicant
Note there seem to be several versions of libnet floating around. There seems be one on freshmeat (http://freshmeat.net/projects/libnet/), and there seems be one on source forge (http://libnet.sourceforge.net/), and there used to be one at packetfactory (http://www.packetfactory.net/libnet) Unfortunately as far I know all of above sites are either defunct or does not have right version of libnet. The one you want you can find,for example, on debian's web site:
http://packages.debian.org/stable/devel/libnet0-dev.html
http://ftp.debian.org/debian/dists/potato/main/source/libs/libnet_1.0.orig.tar.gz
A
local copy is stored here : libnet_1.0.orig.tar.gz
mkdir -p /usr/src/802/libnet cd /usr/src/802/libnet wget http://ftp.debian.org/debian/dists/potato/main/source/libs/libnet_1.0.orig.tar.gz tar zxvf libnet_1.0.orig.tar.gz cd Libnet-1.0/ ./configure make make install
A local copy is stored here : radiusd-02.28.02.tar.gz
Descriptions on how to get cvs tree are at: http://www.freeradius.org/development.html#cvs
basically:
mkdir -p /usr/src/802/radius
cd /usr/src/802/radius
cvs -d :pserver:anoncvs@cvs.freeradius.org:/source login
CVS password: anoncv
cvs -d :pserver:anoncvs@cvs.freeradius.org:/source checkout radiusd
cd radiusd
./configure --prefix=/usr/local/radius
See notes below : [0] [1]
make
make install
See notes below : [2] [3]
/usr/local/radius/sbin/run-radius -X -A
NOTES:
[0]
At this point you will want to modify the Makefile in
the radiusd/src/modules/rlm_eap/types/rlm_eap_tls/ as follows: eap-TLS.Makefile
This necessary in order so that:
a) it will compile EAP-TLS stuff, and
b) it will use the snapshot version of OpenSSL.
[1]
Also, if you are using Linux system at present time
it will missdectedct your gethostbyadd_r() and gethostbyname_r(). Here's one way
to fix it: radius-autoconf.h
Other way to fix is to edit radiusd/src/lib/misc.c file and change the calls
to gethostbyaddr_r() and gethostbyname_r() to have syntax corresponding to this
on Linux.
Yet another way to fix is to modify the configure.in script to
handle those cases.
More info can be found at : http://marc.theaimsgroup.com/?t=101488214000003&r=1&w=2
[2]
At this point you want to configure radius server.
See OpenSSL section to see how to generate keys for free radius.
Now you want to configure your radius stuff at /usr/local/radius/etc/raddb.
Here are some examples how I configured it. Especially important is the diff for
the radius.conf file which has information how to enable EAP/TLS stuff, and how
to setup pathes to appropriate certificate files.
doc/etc-raddb-radius.conf-diff
doc/etc-raddb-client.conf-diff
doc/etc-raddb-users-diff
NOTE: that I set fragment_size to 1750, this is because if I set more
than that the CISCO AIRONET 340 AP will "myseriously" corrupt data, and stop
passing packets, and just display non-descript message:
RADIUS verification failed for Server 192.168.5.200. Probable shared secret mismatch
[3]
Finally you will want to have a wrapper around
radiusd binary.
I would recommend this wrapper script run-radiusd to start radiusd. You will probably want to put it in /usr/local/radiusd/sbin/run-radiusd. Then you can run radius using 'run-radius -X -A' command as shown above.
This script is necessary so that:
a) EAP/TLS module loads right library
libssl, and
b) libssl library loads correct libcrypto.
Especially the
second part seems be some weird bug in OpenSSL where libssl picks wrong library
for some reason.
LD_LIBRARY_PATH takes care of part a), and
LD_PRELOAD
takes care of part b)
update(10/26/2002)::http://www.open1x.org/
You want to make sure it uses stable version of OpenSSL and not the devel version. So it might be be necessary to specify patch to your stable version. for example for RedHat it is : "./configure --with-ossl-root=/usr". (you need to do that only if you put the devel version of openssl in some directory where xsupplicant can find it. that's usually /usr/local/ssl/)
You will need cvs version of xsupplicant as of 1st March 2002 or later. Stable release might be okay if it is dated after this date. You can grab current cvs tarball from http://www.open1x.org/xsupplicant-cvs-current.tar.gz
update(10/26/2002):: http://cvs.sourceforge.net/cgi-bin/viewcvs.cgi/open1x/xsupplicant/
A local copy is stored here : xsupplicant-cvs-current.tar.gz
mkdir -p /usr/src/802/xsup cd /usr/src/802/xsup wget http://www.open1x.org/xsupplicant-cvs-current.tar.gz tar zxvf xsupplicant-cvs-current.tar.gz cd xsupplicant-cvs-current ./configure make make install /sbin/iwconfig eth1 essid rtest See notes below : [a] /sbin/ifconfig eth1 up See notes below : [b] xsupplicant -i eth1 See notes below : [c]
NOTES:
[a]
The client and AP need to be associated first, before
running xsupplicant.
You do association using 'iwconfig <dev> essid
<name>' command.
Alternatively you could set ESSID in
/etc/pcmcia/wireless.opts.
'eth1' is assumed to be the name of device on which your wireless network card is. Adjust as appropriate.
'rtest' is ESSID name of the wireless network you want to connect to.
'rtest' is my test network I created for my own needs. Adjust this as
appropriate.
You need to manually bring the interface up before running xsupplicant.
NOTE: if you forget to do this step xsupplicant will crash.
Once you have done that you need to configure the 1x.conf file (sample can be found source directory for xsupplicant) and put it in /etc/1x .
My sample xsupplicant configuration file can be found at 1x.conf and it can be put in /etc/1x/1x.conf
explanation:
wireless network name is rtest ID to try to login with is adam-ctl (it is same as the one specified in etc/raddb/users file for radius. The three other options (cert/key/root) specify authentication files.
NOTE: at present time xsupplicant does not support DSA based keys.
Assuming you have done all the above, you run it as show before (ie 'xsupplicant -i eth1') assuming your wireless interface is 'eth1'. It will automagically look for the config file in /etc/1x/1x.conf. If you want to put your config file elsewhere, you can use '-c' option to xsupplicant.
equipment used: authentication server - radius server hardware IBM THINKPAD T23 2647-2KU built in 100 Mbps ethernet software Linux Red Hat 7.2 FreeRadius (cvs) OpenSSL (snapshot) authenticator - access point hardware CISCO AIRONET 340 series 11 Mbps ACCESS POINT AIR-AP342E2C Motherboard: MPC860 50MHz, 2048KB FLASH, 16384KB DRAM, Revision 21 100 Mbps ethernet software OS : EnterpriseAP Sys 11.10 supplicant - radius server hardware IBM THINKPAD T23 2647-2KU CISCO AIRONET 340 SERIES 11 Mbps WIRELESS ADAPTER AIR-PCM342 software Linux Red Hat 7.2 xsupplicant (cvs tarball)
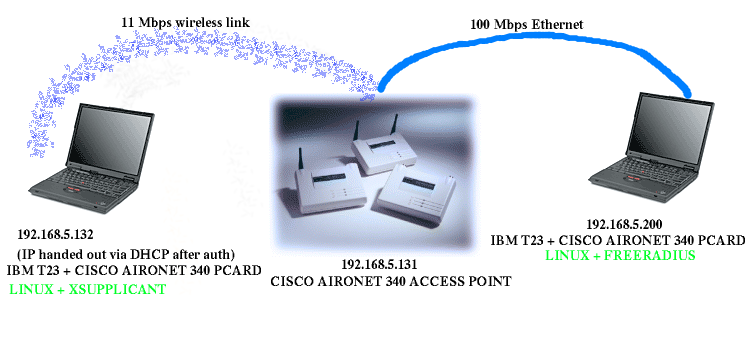
configuration: There are many many ways to set it up. For example at one point I just had two ethernet cards in my laptop and one was connected to AP via cross-over, and the other card was a PcCard which would send data to AP (so the packets would go just in circle :-). Anyway. For the setup described above, which is the same as shown on the picture below: radius server AP ethernet cross over null serial modem I would connect both via mincom (9600 8N1) and mozilla to the AP. Here's how I configured the AP. Access patch: Home -> Setup -> Security -> Authentication ServerHome -> Setup -> Security -> Radio Data Encryption (WEP)
In the above setup I have configured the AP so that the password it uses for radius server is 'whatever', setup the IP for radius server as 192.168.5.200. (the IP for AP is 192.168.5.131).
Also I have run dhcp server to serve IP's but it is not shown in this example as it does not add much to picture.Here's log of server and client authenticating each other. It should be an usefull refernce in case of need to troubleshoot what's going wrong with the connection:
Here I have put example server log with EAP/TLS and TLS part full decoded and
described what each byte means:
server
log - FULL
EAP/TLS : RFC2716 RADIUS : RFC 2865, RFC 2866, RFC 2867, RFC 2868, RFC 2869 TLS : RFC2246
update(11/05/2002)::
update(12/02/2002)::
Corrections, additions, fixes and patches to adam@cfar.umd.edu.
This is not a help desk. You will have better luck asking on FreeRADIUS mailing list.
It is not likely I'll answer any email asking for help as I have since then moved to more exciting things (LinuxBIOS) and I don't even have this setup handy anymore.
However, if you send me ready for inclusion stuff, it is likely that I'll include them in the HOWTO.
update(11/05/2002)::
An list of interesting sites extracted from refer logs:
collections links on EAP/wireless
http://www.hpl.hp.com/personal/Jean_Tourrilhes/Linux/
http://hostap.epitest.fi/links.html
FAQ
http://www.open.com.au/radiator/faq.html
mailing lists
http://lists.cistron.nl/archives/freeradius-users
http://lists.cistron.nl/archives/freeradius-devel
http://lists.bawug.org/pipermail/wireless/
web sites
http://open1x.org/
http://open1x.sourceforge.net/
http://www.freeradius.org/
book on radius
http://www.amazon.com/exec/obidos/ASIN/0596003226/
other HOWTO's (for FreeRADIUS and XP)
http://www.freeradius.org/doc/EAPTLS.pdf
http://www.impossiblereflex.com/8021x/eap-tls-HOWTO.htm
todo: - put eapclient sources - links to RFC's - status of : oddysey beta - status of : windows XP - generate xp-compatibile keys... (maybe just convert to x509!!!!) - setup devel mailing list??? - better fix for gethostby name (as per list archives)